Secure texting through distributed messages
TU researchers enable better protection for sending sensitive information
2024/10/30 by ENCRYPTO/Fleckenstein
In today's digital landscape, ensuring the privacy of online communications is more critical than ever, especially in professions that rely on confidentiality, such as law or politics. Two research groups from the Profile Topic Cybersecurity and Privacy at TU Darmstadt have developed EMC² (Encrypted Multi-Channel Communication), a method that enhances the security of sensitive messages by distributing trust across several existing communication channels. The team's approach addresses the limitations of current encryption solutions, introduces a tool that makes secure communication more accessible, and shows the ineffectiveness of government-mandated backdoors.
Most internet communications today rely on the TLS (Transport Layer Security) protocol, which protects against eavesdropping on the network, but not against access by service providers themselves. While end-to-end encryption (E2EE) ensures only the sender and recipient can read the messages, existing solutions are often not user-friendly or widely adopted. For example, encrypted emails via PGP or S/MIME are difficult for the average user to set up. While apps like Signal offer secure messaging, their encryption is not always visible or well-understood by many users. Additionally, government organisations in the EU and the US have proposed introducing backdoors into encrypted systems, prompting an open letter from more than 300 researchers warning of the dangers of such measures.
Encrypted Multi-Channel Communication
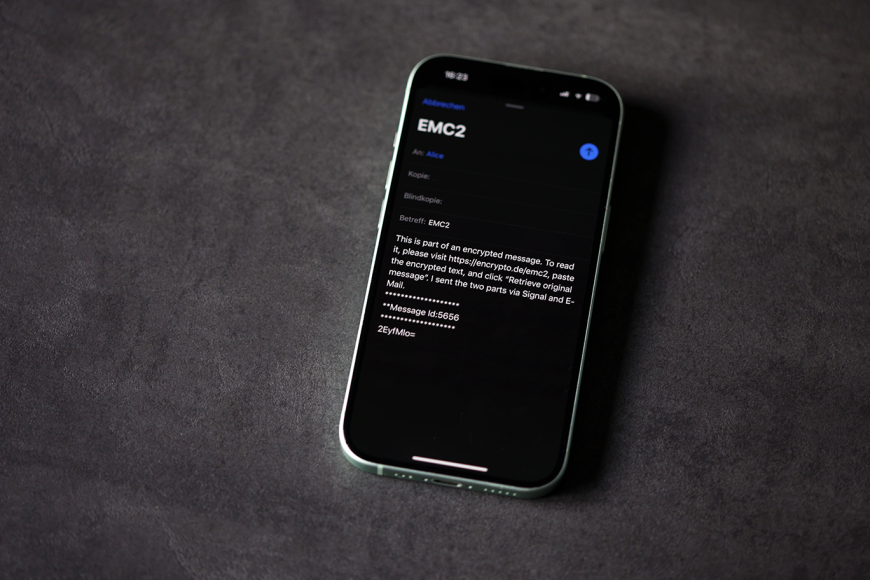
Computer scientists from the research groups ENCRYPTO, led by Professor Thomas Schneider, and PEASEC, led by Professor Christian Reuter, have now developed a solution that balances ease of use, privacy, and security without creating a single point of failure or requiring cumbersome registration processes. The result is EMC² (Encrypted Multi-Channel Communication), which leverages the modern proliferation of messaging apps to distribute encrypted message parts across multiple independent communication channels.
EMC² encrypts a plaintext message in two steps using a technique inspired by the so-called one-time pad encryption. In the first step, the plaintext message is converted into binary form, e.g., the word ‘hello’ into the number 11010. In the second step, these binary numbers are then encrypted using a random sequence of numbers, similar to flipping a coin, where heads means that the numerical value remains the same and tails means that the numerical value is flipped from 1 to 0 or from 0 to 1. The encrypted text and the random sequence of numbers are then sent separately via independent communication channels. The recipient can then use EMC² to enter the two messages and decrypt the plain text. This distributed trust system adds an additional layer of security that ensures that the confidentiality of a message is maintained as long as attackers do not intercept all parts of a message.
Provider independent security
Techniques like EMC² are particularly relevant for sensitive professions such as law, where confidentiality is paramount. The researchers' goal is not to replace existing messaging apps such as Signal, but rather to increase the security of sensitive messages by developing an overarching, independent tool that distributes trust across multiple communication services. The tool developed as part of the research is now available on a public website for anyone interested to try out, along with a video that explains the process in a way that is easy to understand. The solution is independent of individual service providers, requires no registration or set-up, is easy to understand and can be used via existing communication channels. In addition, the proposed method strengthens the argument against governmentally enforced backdoors in messenger apps by demonstrating their ineffectiveness.
The research work was presented on 14 October 2024 at the Workshop on Privacy in the Electronic Society (WPES) during the ACM CCS 2024 conference in Salt Lake City, USA, and was funded by the German Research Foundation through the Collaborative Research Centre CROSSING and the Research Training Group Privacy and Trust for Mobile Users, as well as by the European Research Council (ERC) through the project Privacy-Protecting Services on the Internet (PSOTI).
Publication
Gowri R Chandran, Kilian Demuth, Kasra Edalatnejad, Sebastian Linsner, Christian Reuter, and Thomas Schneider. Encrypted MultiChannel Communication (EMC2): Johnny should use secret sharing. In 23. Workshop on Privacy in the Electronic Society (WPES'24), ACM, Salt Lake City, USA, October 14, 2024. Short paper. [paper] [talk]
The paper has been awarded the CROSSING Collaboration Award 2024. The award is presented annually by the CROSSING directorate for excellent internal collaborative work and outstanding progress in research collaborations within CROSSING.


