GhostTouch: Controlling touchscreens contact-free
Possibility for remote attacks on cell-phones via simulated touch confirmed
2022/02/09
Usually, an action by the user, such as accidentally clicking on a link, is required to install malware on a smartphone. However, scientists from the System Security Lab, lead by CROSSING-PI Prof. Ahmad-Reza Sadeghi, and Zhejiang University have now succeeded in remotely controlling smartphones by imitating touches on the touchscreen.

In an international research project, scientists from the System Security Lab at TU Darmstadt and Zhejiang University in Hangzhou, China, managed, for the first time, to perform targeted attacks on capacitive touchscreens. Using the so-called “GhostTouch”, the researchers were able to use electromagnetic interference (EMI) to simulate touches on the display and thus remotely control the smartphone. In three different attack scenarios, nine out of twelve smartphone models tested could be manipulated.
To realize the attack, the research team had to solve two main technical challenges: First, the difficulty of affecting the touchscreen at all through electromagnetic interference, and second, creating predictable and controllable touches. “In our attacks, we varied the power of the EMI transmitting antenna, the signal frequency, and the distance from the phone display to trigger touches such as taps or swipes with the appropriate signal strength,” explains Richard Mitev, a PhD student at the System Security Lab.
Tricking smartphone users through fake touches

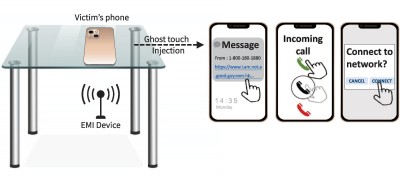
In order to achieve simultaneous controlled touches, the scientists examined the screens of the tested smartphone models in detail in advance. Each device model is based on specific movement patterns for actions such as unlocking, selecting or scrolling. By precisely tuning the parameters of the electromagnetic signal, it was possible to simulate these movement patterns with specifically positioned touches.
Using the “GhostTouch” and the touches it faked, the following threats could be turned into reality in practical attack scenarios. The injection of malware: If the attacker knows the phone number of his victim, he can send a message containing a malicious link, for example. If the phone displays a notification for the received message, the attacker can open the notification using the “GhostTouch” and click on the link to download, for example, the malware that is embedded in the link.
In addition, the attacker can establish a sneaky connection via WiFi or Bluetooth. For example, he can control the phone with a Bluetooth mouse or perform a man-in-the-middle attack, which can be used to capture communications. In the third scenario, the attacker accepts a call via “GhostTouch” so that an eavesdropping attack can be launched and the victim can be bugged.
Modern touchscreens are vulnerable
Although modern screens are subjected to careful electromagnetic tests and feature a protective anti-interference design, it was possible to generate targeted, contactless touches on nine of the twelve smartphone models tested and thus implement attacks. This demonstrates that the functionality of even the most modern touchscreens can be manipulated under certain conditions using the right equipment, and that they should not be blindly trusted.
Publication
GhostTouch: Targeted Attacks on Touchscreens without Physical Touch (opens in new tab) by Kai Wang (Zhejiang University), Richard Mitev (TU Darmstadt), Chen Yan (Zhejiang University), Xiaoyu Ji (Zhejiang University), Ahmad-Reza Sadeghi (TU Darmstadt), and Wenyuan Xu (Zhejiang University).
The research results will be presented at the top conference USENIX Security Symposium which takes place from August 10 to 12, 2022 in Boston, USA.


